IP Marketing
Practical Digital Cyber Security
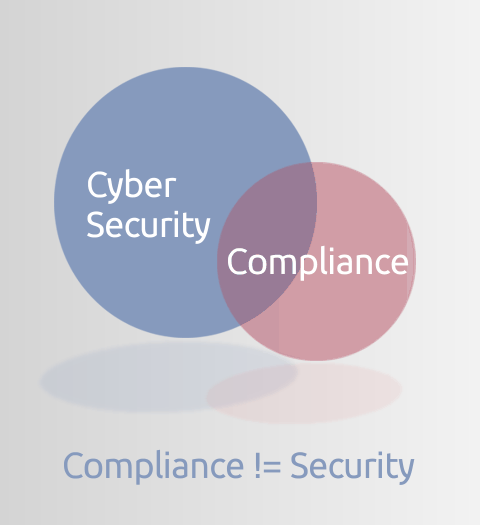
Security not Compliance
Organisations invest in cyber security to protect their data.
Compliance provides some reassurance controls are in place, but compliance is not the objective; remaining secure is the objective. Many confuse the two

Digital Cyber Security innovation
We believe that you cannot stand still in digital cyber security.
Attack methods are continually evolving and so consequently it's necessary to continually evolve new control mechanisms to keep ahead

Change is essential
The slower you move, the easier target you become for an attacker.
Change involves risk, but changing too slowly is the greatest risk of all
Continuously Test
Don't just believe you're secure because you have deployed some control or cool technology.
Continuously test to ensure what you believe is working, is working, and isn't missing important signals
Solutions we have delivered
Team & Capability Building
Creating digital cyber teams and capability from a standing start
We have built digital security teams and capability from scratch.
Our work has included running cyber security reviews to establish a baseline. Then from the results of such reviews, building cyber maturity improvement programmes and continually reviewing these programmes to reflect changes in the cyber security threat landscape.
We have created Target Operating Models (TOMs), recruited and organised digital security teams against these TOMs and produced effective and highly-motivated digital cyber security teams.
WAF & DDoS mitigation
Web Application Firewall and Distributed Denial of Service protection
We have scoped, shaped, designed, delivered and configured web application firewall (WAF) and distributed denial of service (DDoS) protection services for a number of customers. These have included a major UK Government Department and a large UK-based multinational insurance company.
Our involvement has included extensive research and selection of available technologies, followed by design and deployment of solutions based on Akamai Kona Site Defender, a technology in which we have considerable experience.
DMARC & Fraudulent Email countermeasures
Stopping fraudsters deliver phishing Email to customers and staff
We designed a pattern of counter-fraudulent Email (spam and phishing mail) for a major UK Government department which was suffering significant brand abuse problems. The 'pattern' included a combination of SFP, DKIM, ADSP and DMARC, along with domain name usage rationalisation and general 'Email hygiene' improvements. The programme is credited with blocking in excess of 300 million phishing Emails in 2016 alone.
The pattern has gone on to be generally accepted by the UK Government and is incorporated in advice provided by the UK Government's GDS (Government Digital Service) function.
We have also implemented the same pattern of controls into other businesses, helping them counter fraudulent and phishing Email both to customers and to staff.
Secure web application development
Ensuring web applications are secured from malicious manipulation
We have developed programmes to improve web application security through a combination of automated code analysis using tooling such as Checkmarx, dynamic test tooling including Detectify and OWASP Zap, development pipeline checks and creation of development team continuous education and awareness programmes.
Staff Security Awareness Programmes
Making all staff aware of potential security risks, both in their work and personal context, is increasingly important as attacks become more sophisticated and harder to identify. We have selected and introduced monthly cartoon-based security awareness programmes including hugely popular monthly cartoon videos from Ninjio that proved not only to be effective, but popular, with colleagues not included in the programme asking to be included.
Cyber Innovation
We believe in continually reviewing new technologies and seeing how we can deploy these to maintain state-of-the-art cyber defence. Technologies we have worked with include:
Zero Trust
We developed a multi-layer zero trust model, not simply based on zero trust around compute resources, but logically segregated workstations, so that workstations only connect to resources the user needs to access.
The model creates a series of logical 'security zones' with logical workstations apparently connected to different networks hosting different resources. Importantly, different 'styles' of computing by the same user are handled in different security zones.
The model provides a logical equivalent to multiple networks operating at different security markings, but without the duplication of equipment. When layered with sophisticated intrusion detection technology, multiple layers of user and device verification, user access authorisation, compute isolation and segregation plus application data access monitoring, you have a true multi-layer zero-trust architecture to protect your critical data assets and enhance the security of systems
Who we have helped
Organisations where our staff have helped include...
Get in Touch
Interested in whether we could help secure your digital businesses?
 IP Marketing is a boutique digital cyber security consulting business. Our speciality is building digital cyber security capability within organisations. Our guidance helps organisations to secure online systems, including both web and Email. We emphasise effective security solutions over 'controls compliance' and consider ourselves both technically and business aware.
IP Marketing is a boutique digital cyber security consulting business. Our speciality is building digital cyber security capability within organisations. Our guidance helps organisations to secure online systems, including both web and Email. We emphasise effective security solutions over 'controls compliance' and consider ourselves both technically and business aware.






